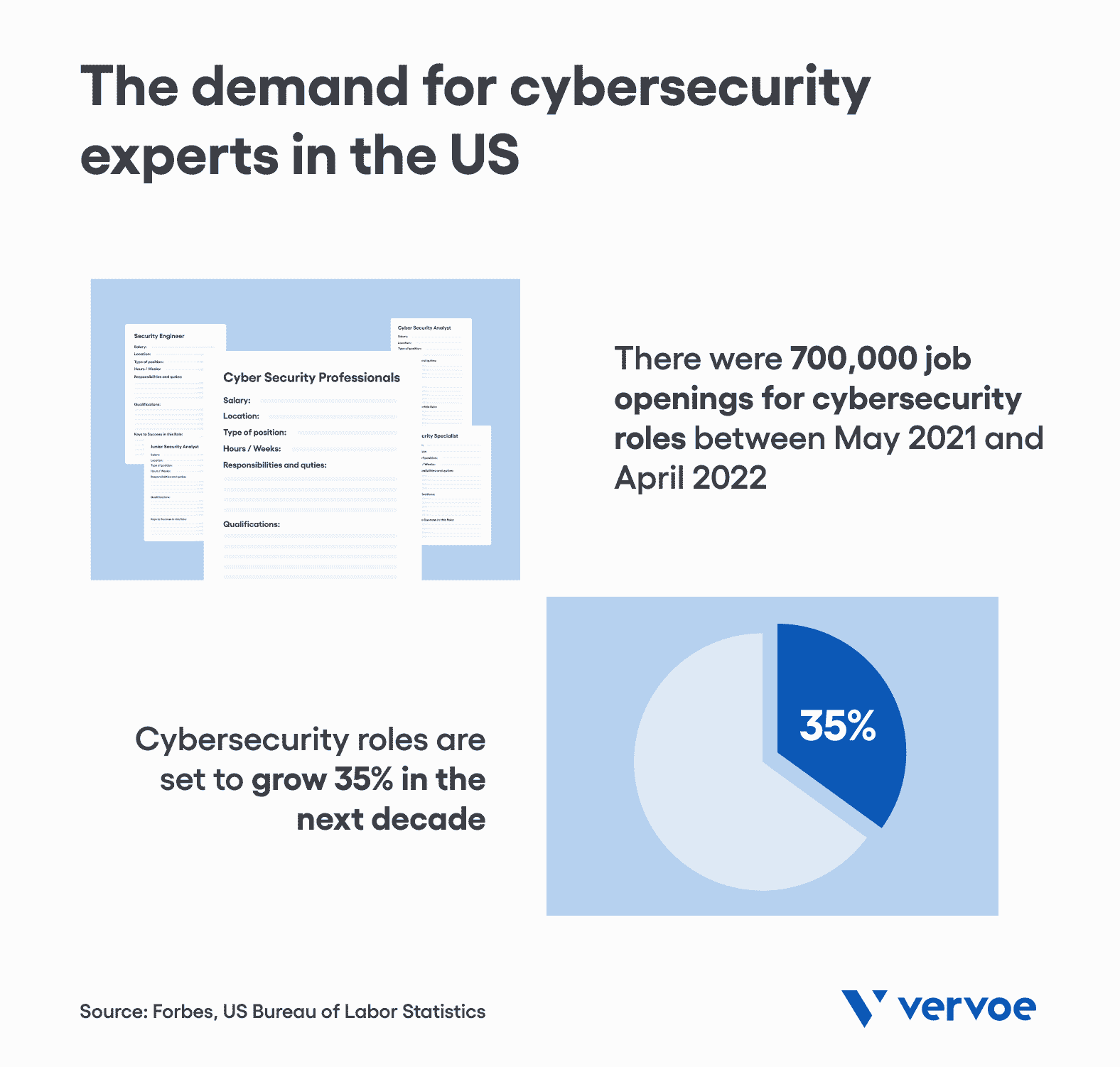
Cybersecurity is one of the fastest-growing industries in the world.
In the US alone, there were more than 700,000 job openings for cybersecurity roles between May 2021 and April 2022. And this is showing no sign of slowing down any time soon — according to the US Bureau of Labor Statistics, cybersecurity roles are set to grow 35% in the next decade. To put this into perspective, the average growth rate for all occupations is just 4%.
Whether you’re a large organization wanting to protect your most significant assets or a small business concerned about the severity and frequency of cybercrime, there are plenty of reasons to consider hiring cybersecurity professionals.
In this article, we’ll unpack the mysterious nature of the cybersecurity industry, break down common cyber roles, and delve into the most important skills for cybersecurity — hard and soft — that will set aside top-performing professionals from the rest.
Why does cybersecurity matter more than ever?
Cybersecurity is a growing issue affecting individuals and organizations in all corners of the world. Unfortunately, in recent years, cybercrime has intensified, putting tremendous pressure on organizations to prioritize security resources to mitigate the risk. Yet, according to a Center for Strategic International Studies (CSIS) report, 82% of organizations lack cybersecurity skills.
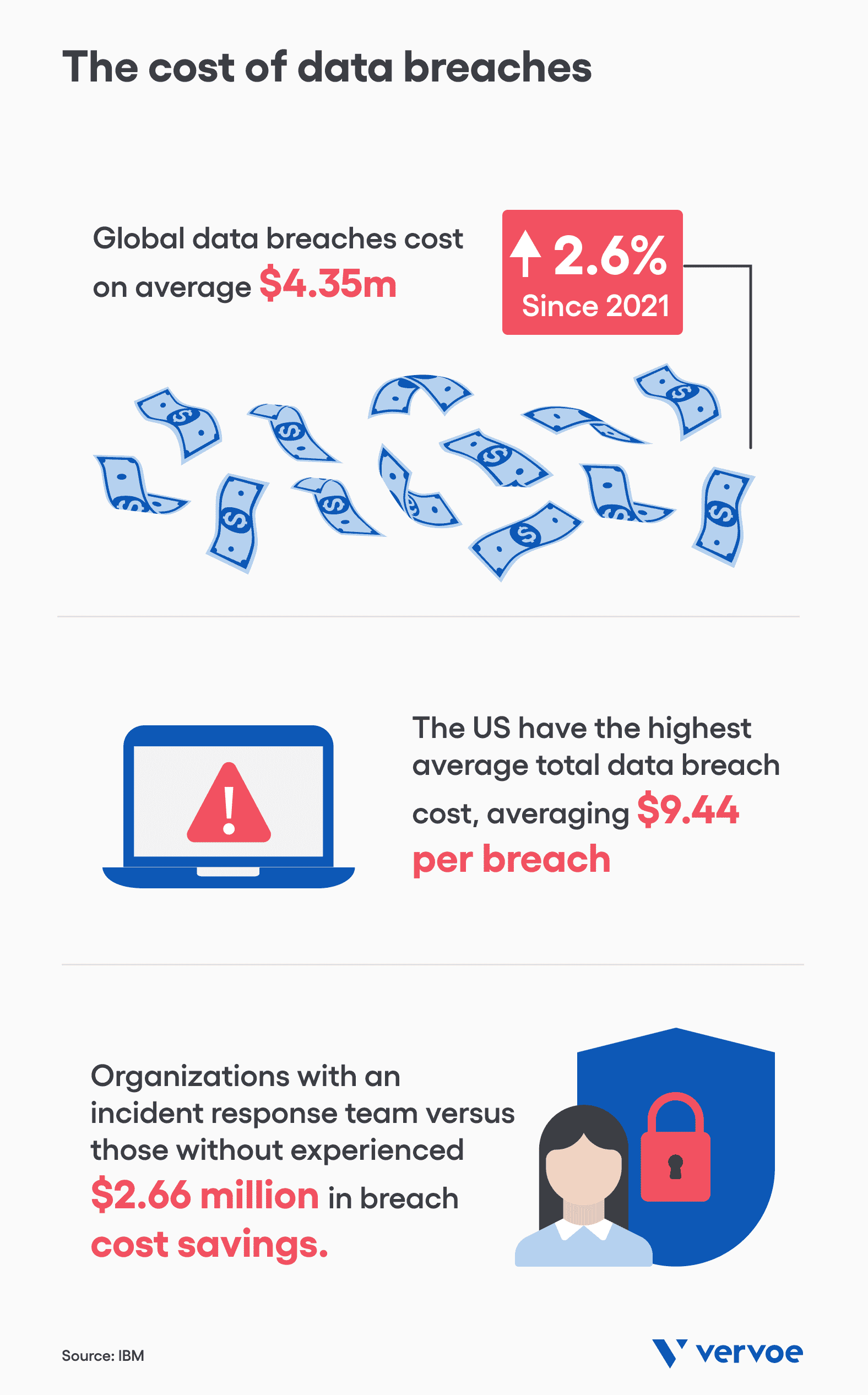
Consider the following statistics from IBM’s Cost of a Data Breach Report 2022:
- Global data breaches reached an all-time high in the last year, with the cost of a violation averaging $4.35 million in 2022. This is a 2.6% increase in data breaches from 2021 and a 12.7% increase from 2020.
- The United States continues to have the highest average total data breach cost, costing US businesses, on average, $9.44 million per breach. This is a 4.3% increase since 2021.
- For the 12th year in a row, the healthcare industry represented the highest cost for data breaches. The average total cost of a healthcare breach increased from $9.23 million in 2021 to $10.10 million in 2022 — a 9.4% increase.
- There is a strong correlation between organizations with largely remote workers and higher data breach costs. The average cost of data breaches for organizations with 81-100% of remote workers was $3.99 million, compared to $1.11 million for those with less than 20% of their employees working remotely.
- On average, organizations with an incident response team that tested an incident response plan versus those without experienced $2.66 million in breach cost savings.
6 in-demand cybersecurity roles — and hard and soft skills to look for
1. Chief Information Security Officer (CISO)
What does a CISO do?
A Chief Information Security Officer, more commonly known as a CISO, is a senior-level cybersecurity officer responsible for developing, implementing, and maintaining an information security program for an organization. As part of their role, this may include:
- Building a security team to help them deliver upon the strategy.
- Developing and maintaining procedures and policies to help protect communications, systems, and assets.
- Ensuring compliance with applicable laws and regulations.
- Interacting with stakeholders concerning information security issues and solutions.
Additionally, according to Evanta’s 2022 Survey Report, a CISO’s top priorities in 2022 are cloud security, strategy and architecture, third-party risk management, measuring and communicating risk, user access/IAM, and security operations.

Whether you’re considering a cybersecurity career or striving for more progression to reach an executive level, a CISO is generally considered the most senior-level position in one’s cyber career path and is generally the final stop for many industry professionals.
What hard and soft cybersecurity skills are required to be a CISO?
CISO hard and soft skills
| Hard skills | Soft skills |
| IT skills and cybersecurity knowledge | Strong communication and presentation skills |
| Security incidents management | Drive and determination |
| Business expertise | Leadership and supervisory skills |
| Risk assessment management | Forward-thinking |
| Policy development and administration | Analytical |
| Knowledge of regulation and compliance with standards | Collaboration and conflict management |
| Security operations | Interpersonal skills |
2. Security Architect
What does a Security Architect do?
A Security Architect is a senior-level role responsible for helping design, build and maintain an organization’s security system to help safeguard employees, data, and client information. A Security Architect’s daily responsibilities will be largely influenced by the size and structure of the organization they’re working for. As a general idea, duties may include:
- Designing a security strategy.
- Overseeing/managing projects to improve security.
- Leading/managing security testing strategy (i.e., vulnerability scanning, penetration testing, etc.).
- Regularly undergoing threat analyses.
- Leading/managing a team.
- Ensuring compliance with applicable laws and regulations.
Due to the seniority of a role like Security Architecture, many candidates enter the field via an alternative role. As such, entry-level roles like Cybersecurity Analysts, Security Specialists, and Incident Responders are a great way to enter the industry, building up relevant skills for those interested in pursuing a career in Security Architecture.
What hard and soft cybersecurity skills are required to be a Security Architect?
Security Architect hard and soft skills
| Hard skills | Soft skills |
| Cloud security skills | Collaboration |
| Network security skills | Project and team management |
| Software development and DevSecOps | Written and verbal communication |
| Identity and access management | Problem-solving and analytical |
| Scripting language | Integrity |
| Linux, Windows, and Mac operating systems | Ethical |
3. Cybersecurity Engineer
What does a Cybersecurity Engineer do?
Cyber Engineers may also be referred to as Data Security Engineers, IT Security Engineers, and Web Security Engineers.
Cyber Engineers combine electrical engineering and computer science skills to create and manage hardware, software, and security policies designed to keep computers, networks, and information safe. Essentially, their role is centered around developing and executing security solutions to minimize the impact of hackers, cyberattacks, and threats.
A Cybersecurity Engineer’s daily tasks will vary from organization to organization, based on industry, size, and team structure. According to HBU, a Cybersecurity Engineer’s duties may include the following:
- Handling a network of system security breaches and viruses.
- Designing, implementing, and testing security measures to protect systems, networks, and data.
- Reporting and communicating with various departments.
- Performing penetration testing to identify system and network weaknesses.
- Working with IT experts to modify or strengthen computer code to address weaknesses.
- Penetration testing to understand network, application, and data system vulnerabilities.
- Installing, testing, and configuring networks.
What hard and soft cybersecurity skills are required to be a Cybersecurity Engineer?
Cybersecurity Engineer hard and soft skills
| Hard skills | Soft skills |
| Coding (i.e., proficiency in Python, C++, Java, Ruby, etc.) | Analytical |
| Firewall and intrusion detection systems | Problem-solving |
| Knowledge of operating systems | Teamwork and collaboration |
| Security protocols | Creative thinking |
| Cybersecurity tools | Communication |
| Mathematical skills | Attention to detail |
| Engineering knowledge | The ability to work under pressure |
| IDS/IPS, penetration and vulnerability testing | Time management |
4. Malware Analyst
What does a Malware Analyst do?
As the name suggests, a Malware Analyst is responsible for examining, identifying, and understanding various cyber security threats, including viruses, worms, bots, rootkits, and trojan horses, according to Infosec Institute.
While responsibilities and expectations will depend on the size and structure of the organization, a Malware Analyst is commonly responsible for one or more of the following:
- Responding to incident reports.
- Recommending and implementing changes to support system recovery.
- Responsible for preventing malware attacks.
- Staying up to date on the latest malware and software updates.
- Communicating with the security team about any vulnerabilities or changes to the system.
- Creating security policy documentation.
Malware Analysts are said to combine the skills of a programmer and a cyber detective. Many Malware Analysts will have a background in cybersecurity, computer science, or programming.
What hard and soft cybersecurity skills are required to be a Cybersecurity Engineer?
Cybersecurity Engineer hard and soft skills
| Hard skills | Soft skills |
| Knowledge of operating systems and networking | Creative thinking |
| Knowledge of security principles | Strong communication skills |
| Skills in programming | Determination |
| Identify, contain, disassemble, and mitigate zero-day malware | Curiosity |
| Proficiency in coding (to be able to reverse engineer code) | Analytical |
| Proficiency in programming language (to work with high-level languages) | Critical thinking |
5. Penetration Tester
What does a Penetration Tester do?
Penetration Testers are responsible for identifying and fixing security weaknesses impacting an organization’s digital assets and networks. Generally, a penetration test will mimic a cyber attack, whereby the tester will seek to hack the computer system to exploit potential weaknesses and vulnerabilities to suggest improvements to strengthen the security. A Penetration Tester is also known as a “good hacker” or “ethical hacker.”
Penetration Testers often use a five-step process to facilitate testing. According to Imperva, this includes:
- Planning — The penetration tester defines test goals and gathers relevant information.
- Scanning — The penetration tester uses scanning tools to gain greater insight into how a target may respond to threats.
- Access — The penetration tester stages a web attack to reveal the organization’s weaknesses.
- Access maintenance — The penetration tester imitates APTs to see if the uncovered weaknesses can be utilized to maintain system access.
- Analysis and configuration — Based on the results, the penetration tester will configure WAF settings and conduct more tests to assess vulnerabilities.
Like all cybersecurity roles, the Penetration Tester’s responsibilities and daily duties will depend on the organization’s size and structure. However, here are a few common responsibilities:
- Investigate and experiment with different cyberattack methods.
- Carry out penetration tests on apps, cloud infrastructure, and network devices.
- Design and implement penetration testing methodologies.
- Assess and amend code to improve security weaknesses.
- Document security and compliance issues.
- Automate relevant testing techniques to ensure efficient processes.
- Gather findings and recommendations to report to stakeholders.
- Reverse engineer malware and spam.
What hard and soft cybersecurity skills are required to be a Cybersecurity Engineer?
Penetration Tester hard and soft skills
| Hard skills | Soft skills |
| Programming languages (i.e., Python, BASH, Java, Ruby, Perl, etc.) | Problem-solving |
| Comprehensive knowledge of network and application security | Written and verbal communication |
| Unethical hacking techniques | Collaboration and autonomy |
| Threat modeling | self-motivated |
| Pentest management platforms | Strong aptitude |
| Linux, Windows, and MacOS environments | Analytical |
| Security assessment tools | Creativity |
| Cryptography skills | Ethical |
Why do cybersecurity skills matter?
Historically, many candidates would find their way into a cybersecurity career by obtaining a bachelor’s or master’s degree in a related field — including computer science, IT, cybersecurity, electrical engineering, and more.
Yet, the growing global shortage of qualified cybersecurity professionals has forced organizations to reassess what’s truly important for a candidate to succeed in the role, recognizing that candidates may have obtained their skills through alternative pathways or self-teaching. This allows employers to gain access to a broader talent pool and improves diversity by making the role accessible to underrepresented candidates.
Many employers are now relying on skills testing and job simulations to assess candidates from all walks of life to understand if they have what it takes to thrive in the role and within the company’s environment. To do so, organizations need to know what hard and soft skills are fundamental to the role’s success.
Vervoe’s AI-powered skills assessment platform effectively allows organizations to add confidence to their hiring decisions. Through our ready-made assessments and completely customizable options built from scratch, Vervoe’s skills validation platform reassures employers that the chosen candidate has the skills required to do the job while giving applicants a realistic job preview.
Final thoughts
Cybersecurity poses an undeniable threat to organizations of all sizes. The reality is: cybercrime is on an upward trajectory, requiring companies to take a pragmatic approach to safeguard their digital assets.
In 2022, cybersecurity professionals are lacking in just about every job and industry. Yet, demand is growing particularly fast in certain roles — including Chief Information Security Officers (CISO), Security Architects, Cybersecurity Engineers, Malware Analysts, and Penetration Testers.
While many cybersecurity skills are transferable across various roles, including collaboration, ethics, and proficiency in operating systems and networks, many roles require candidates to have a fundamental understanding of more niche technical skills, such as threat modeling and engineering proficiency.
Therefore, organizations must thoroughly understand the cybersecurity skills needed for candidates to succeed in open roles, accompanied by proper measures to confidently validate said skills. AI-powered skills testing platforms like Vervoe are a great way to add confidence to the hiring process.