So you need to hire a cybersecurity expert, but are you confident in how to spot a good candidate? Remove the guesswork, and use role specific job simulations.
According to a recent Gartner survey, security and risk management, application and integration strategies, and infrastructure and operations were the top three technology priorities for midsize enterprises (MSEs) in 2022.
“MSEs are shifting investments and even increasing budgets to fund their top technology priorities,” said Mike Cisek, VP Analyst at Gartner. “However, the accelerated rate of change in security, infrastructure, applications, and cloud ecosystems complicates the selection of new tools.”
In layman’s terms, if business leaders don’t prioritize cybersecurity in the immediate future, client bases, reputations, and yes, finances are on the line. In today’s digital landscape, you would be hard pressed to find an organization who could afford not to take cybersecurity seriously.
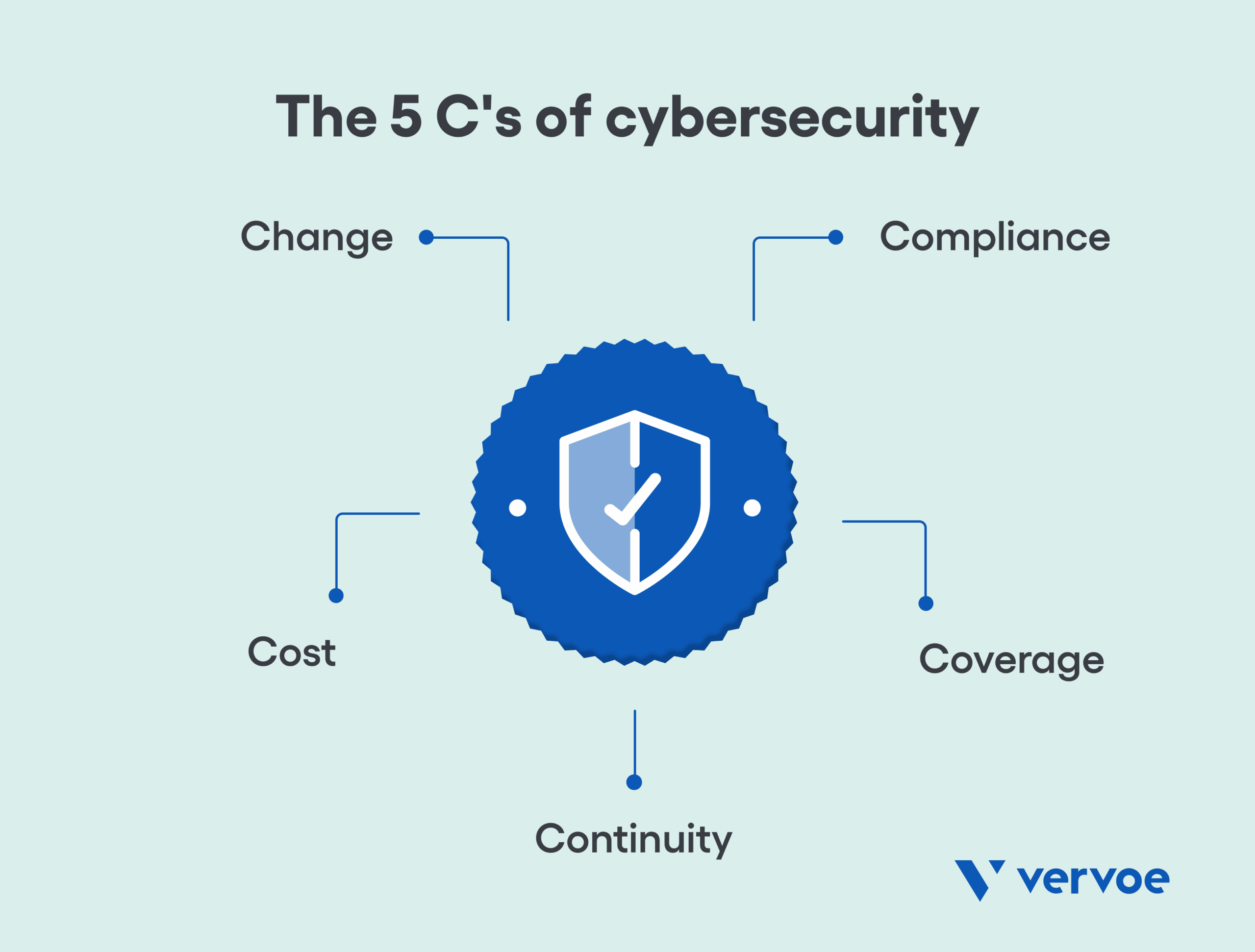
The five C’s of cybersecurity are five areas that are of significant importance to all companies of all shapes and sizes: change, compliance, cost, continuity, and coverage. The catch? Prioritizing cybersecurity almost certainly means adding an expert in this field to your team.
As Apple recently discovered, outsourcing connects your business to a third party, which can raise unexpected security and privacy risks. Unfortunately, IT recruitment solutions leave a lot to be desired when it comes to validating the skills of top cybersecurity talent: until now.
What should an effective cybersecurity skills assessment cover?
You shouldn’t have to be a cybersecurity expert in order to hire a cybersecurity expert. Terms like firewall, HTML, and SSL certificates may mean nothing to a recruiter or hiring manager but are essentials in the world of cybersecurity.
It’s for this reason that a growing number of organizations are rethinking the hiring process as a means to attract top talent via the use of job simulations. Not everyone has the skills to identify the right cybersecurity professional for the job, but using immersive experiences that can verify and validate a candidate’s experience and suitability for a role, and deliver clear-cut results.
So what type of person is good for cybersecurity, and what should a cybersecurity skills assessment cover? The obvious answer is someone who identifies as a critical thinker, has an eye for detail, and is good with computers. In reality, the work itself is so broad that the ideal candidate will usually vary depending on the needs of the company, and what the day-to-day tasks look like.
Regardless of the level of work required, the good news is that there are some standard core skills for cybersecurity that almost every industry professional should embody as a bare minimum.

Essential cybersecurity technical skills to verify
It’s worth keeping in mind that the specific skills required for cybersecurity will vary somewhat from one career to the next, especially as there are many different kinds of cybersecurity positions. Broadly speaking, cybersecurity technical skills to look for should include:
- A functional understanding how operating systems are built and managed
- A firm understanding of the fundamentals of computer networking and cloud computing
- An ability to being able to build and evaluate network architecture,
- Proficiency in programming languages like Java, Python, and C++
- Familiarity with MySQL database platforms
- Understanding protocols for detecting and preventing firewall breaches
- Firm understanding of basic antivirus principles, VPNs, and firewalls
- Mastery of security audits
Thankfully, job simulations can take care of this on your behalf. By assessing an applicant’s skills in a simulation that mimics real life settings and are directly relevant to all things cybersecurity, hiring managers can rest easy knowing that the basics have been validated — but what about soft skills?
Less common soft skills for cybersecurity professionals
As outlined above, hard skills are technical skills that enable a worker to complete certain tasks at a particular level of mastery, producing specific, measurable results. In comparison, soft skills are personal skills that an individual brings to the workplace, but they’re not bound to any specific job. To further complicate matters, the latter are metrics that are usually a lot harder to measure.
According to the World Economic Forum, the average half-life of skills is only four years. If a cybersecurity expert wants to retain their level of technical skills over the long term, then they also need to have a soft skill of continuous learning.
This is because cybersecurity is a field that is constantly evolving, and requires vigilance in staying compliant and knowledgeable about changes as they develop. Anyone who enters the field will have to be committed to learning new cybersecurity skills to keep pace with the change in technology — even if that means learning an array of entirely new skills consistently throughout your career. Cybersecurity experts can’t afford to rely on the information they already know.
As with most tech jobs, cybersecurity positions often involve working on a team, which often requires attributes of strong communication soft skills. These roles also require interacting with people who don’t share the same level of technical expertise, so being able to explain what kind of solutions might be most appropriate for any given problem is a must.
Networking soft skills are another important skill set to develop in cybersecurity. Being able to share ideas and theories with like-minded individuals is an excellent way to further advance your own skills in the industry, and can also be applied to solving problems. While they may not get as much attention as the technical stuff, soft skills for cybersecurity are still important for finding the right hire.

6 key job simulations to test cybersecurity skills
Now that you know what hard and soft skills to look for when hiring a cybersecurity expert, the next step is to ensure that you have the right recruitment protocols in place. Traditional recruitment methods like resume screening and psychometric testing are almost irrelevant when it comes to identifying top talent, as they fundamentally lack the ability to assess and validate skills.
At Vervoe, we’ve launched our own cybersecurity skills assessment that focuses on six job simulations for these types of highly skilled roles. Our technology allows recruiters and hiring managers to place candidates inside a live terminal to complete a range of job specific tasks, such as configuring firewall systems, patching vulnerabilities, hardening operating systems, and investigating intrusions.
Years in the making, our cybersecurity job simulations have been built from the ground up to ensure that only the most relevant skills are assessed so that companies can make data-driven decisions when hiring an in-house cybersecurity expert. In simple terms, we’ve done the work so that you don’t have to.
The simulator tests a range of skills related to success in cybersecurity like attention to detail, problem-solving, communication, and risk management through common scenarios they’ll face on the job.
While we understand that no two cybersecurity roles are ever quite the same, the simulator enables you to hire an expert with confidence – so what are your options?
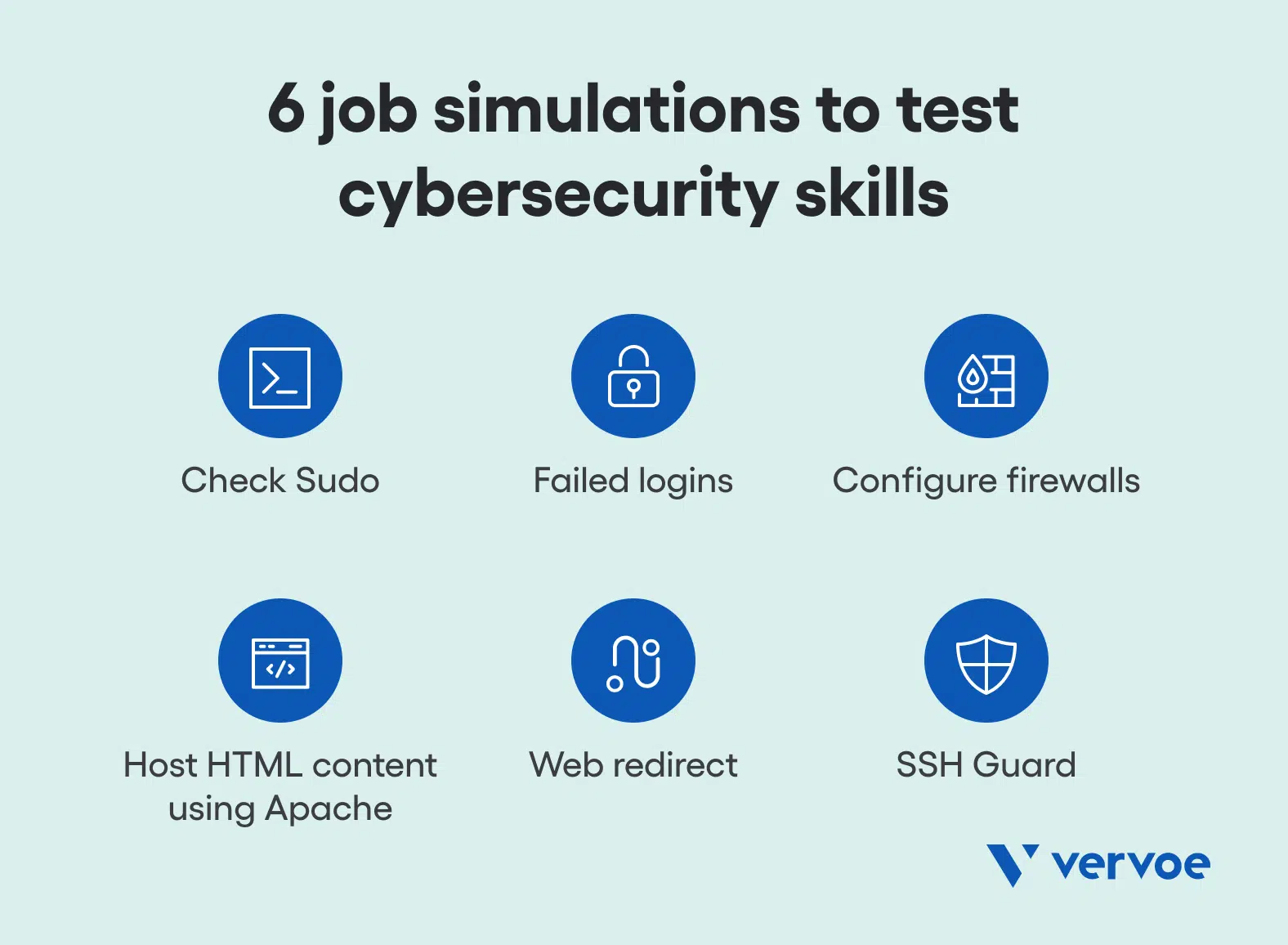
1. Check Sudo
Suitable for junior roles, this job simulation allows candidates to check which users and/or programs can run as root with Sudo. Skills assessed include basic Linux skills, the ability to identify users that can use privilege escalation, and the ability to identify programs that can run with elevated privileges. Ranked as a basic cybersecurity skills assessment, the estimated time to complete is just five minutes.
2. Failed logins
As another job simulation ideal for a junior or entry-level cybersecurity position, in this job simulation, a candidate must identify failed logins and what user(s) they were associated with. While also assessing basic Linux skills, it also tests the knowledge of log files in Linux and where to find them, and the candidate’s ability to review a log file and extract the required information.
3. Configure firewalls
For a slightly more difficult entry-level job simulation that assesses cybersecurity technical skills, the candidate must reconfigure the default configuration of a Linux firewall, and only permit ssh and http services on the internet-connected interface, via the default/active firewall profile. The configuration must be based on predefined services configuration already available and must persist across reboots.
4. Host HTML content using Apache
Ideal for mid-weight roles, in this job simulation candidates must ensure that provided web content by leveraging the web server available on the web host, while doing so ensure the content is owned by the least privileged content available, with the appropriate permissions. Ranked as a 3/5 difficulty, a candidate can showcase their skills in both Linux and Apache simultaneously.
5. Web redirect
For a slightly more difficult cybersecurity skills assessment, candidates create an SSL certificate and harden Apache. Candidates must ensure the content currently provided using http, should now be available under https, as well any user trying to access the content over http is permanently redirected to https. In doing so, the candidate will need to create a self-signed certificate and secure it appropriately.
6. SSH Guard
As a key tool to prevent brute force login attacks, this job simulation is ranked 4/5 for difficulty. Over an estimated 15-minute period, candidates must set up ssh-guard, be able to use a bastion host, and setup ssh-guard on the internally visible ssh-host, while ensuring that its systems logs are visible remotely on the bastion host. By using the live terminal, it’s a great way for candidates to display their Linux knowledge.
With our intelligent scoring system and rich candidate profiles that allow hiring managers to truly understand what went into a candidate’s overall score without spending hours reviewing, using job simulations for efficient cybersecurity recruitment is undoubtedly the way of the future.
Meet the experts on cybersecurity and IT recruitment solutions
Vervoe is an end-to-end solution that is proudly revolutionizing the hiring process. By empowering companies to create assessments that are tailored to suit the specific requirements of a role, Vervoe predicts performance using job simulations that showcase the talent of every candidate.
By assessing an applicant’s ability to perform the role through a skills assessment, our job simulations focus on the work — and not the person. To see people do the job before they get the job, request job simulation test examples or book a demo today and let our experienced team run you through Vervoe’s full range of ready-made and tailored solutions.